Work in
Harmony
Axis ensures that your connectivity is always secure, and in-sync, with your business.
Secure the modern workplace with SSE
Stop struggling to secure business access, connect your modern workforce with a powerful Security Service Edge (SSE) platform, ensuring secure access and elegant connectivity.
Hybrid
work
Make work from anywhere seamless and secure regardless of location, device, or network.
Modernize
infrastructure
Reduce dependence on legacy appliances and create a secure, cost-effective network with cloud.
Introducing the
Atmos Platform
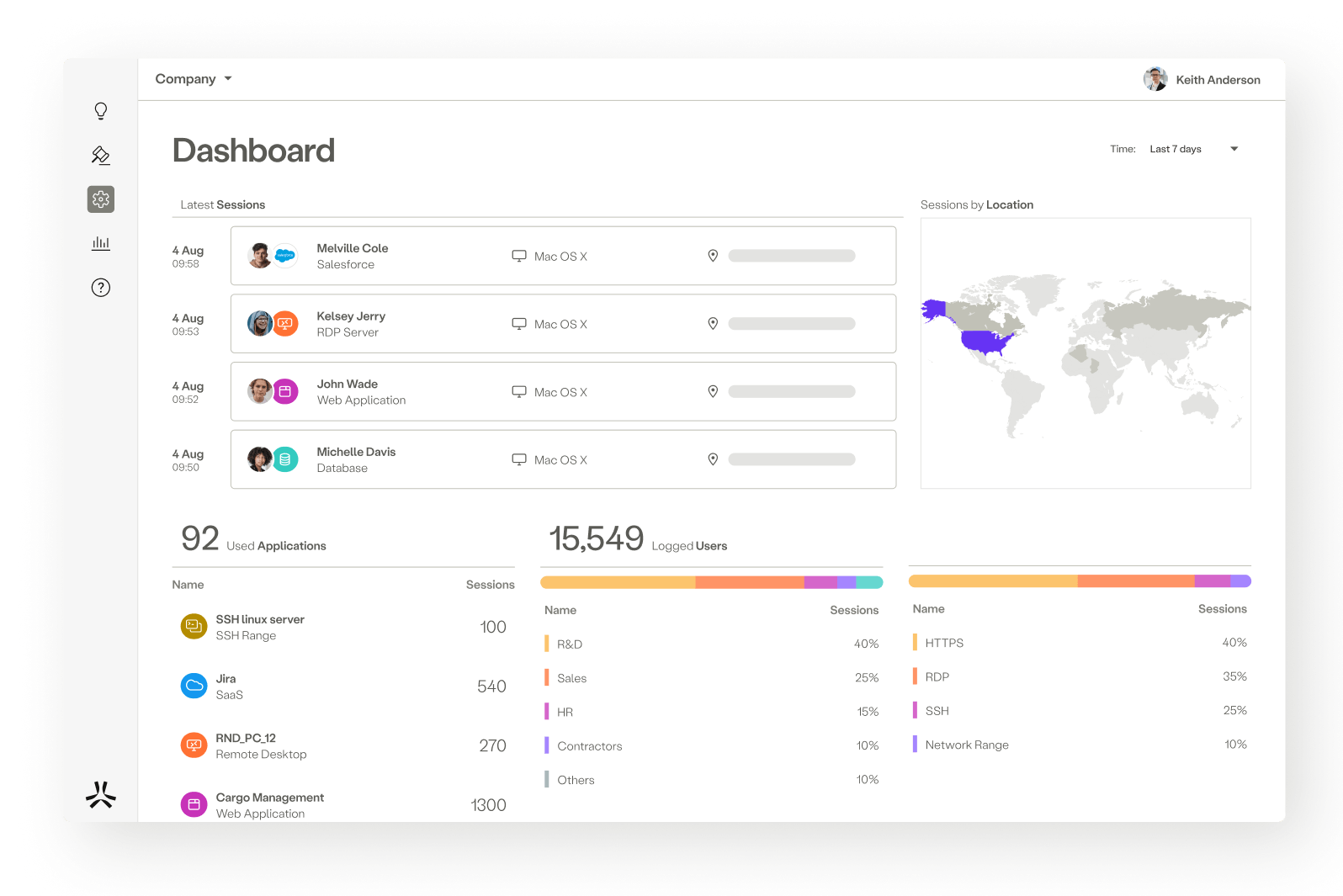
The full force of ZTNA, SWG, CASB, and DEM composed into one.
Full SSE Platform
Atmos
Atmos by Axis is the first Connectivity-as-a-Service platform to elegantly integrate ZTNA, SWG, CASB and Digital Experience into a single, easy to use, interface.
Atmos ZTNA
Atmos ZTNA is the most advanced ZTNA in the industry, delivering zero trust access to all private applications (even VOIP, AS400, & ICMP).
Atmos Web Gateway
Atmos SWG enables zero trust access to the Internet through advanced SSL inspection, URL filtering, Malware Scanning, and DNS filtering.
Atmos CASB
Atmos CASB mediates secure connectivity to SaaS apps, ensuring sensitive data remains protected, while preventing cyberthreats
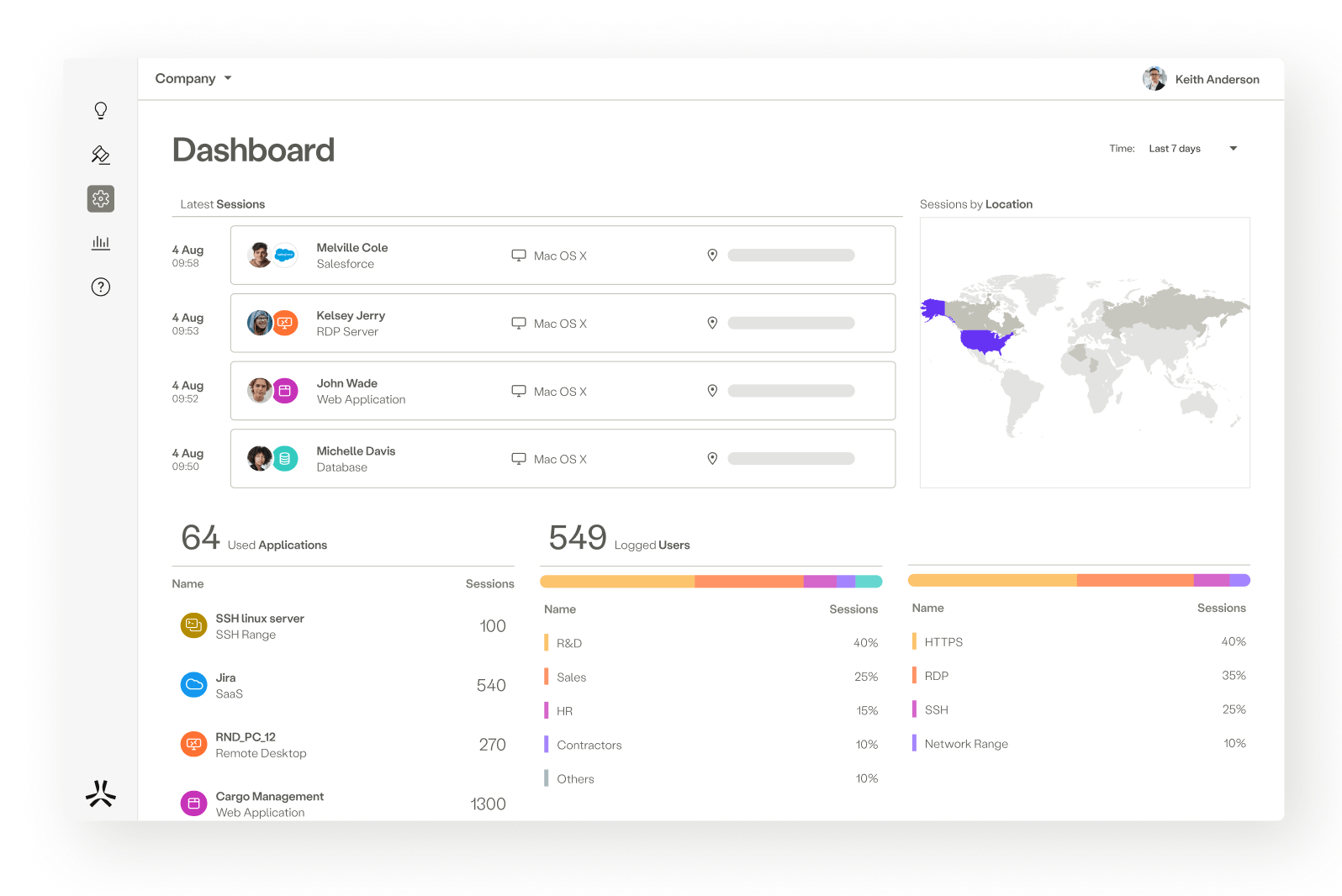
Atmos Experience
Atmos Experience provides in-depth monitoring of device, app, and network performance so IT can easily pinpoint connectivity issues.
Full SSE Platform
The power of one
Make life easier with one UI, one policy, and every SSE capability you need baked into every PoP.
Secure access to any business resource
Atmos allows you to secure access to the Internet, 10,000+ SaaS apps, and private resources for all users or headless devices.
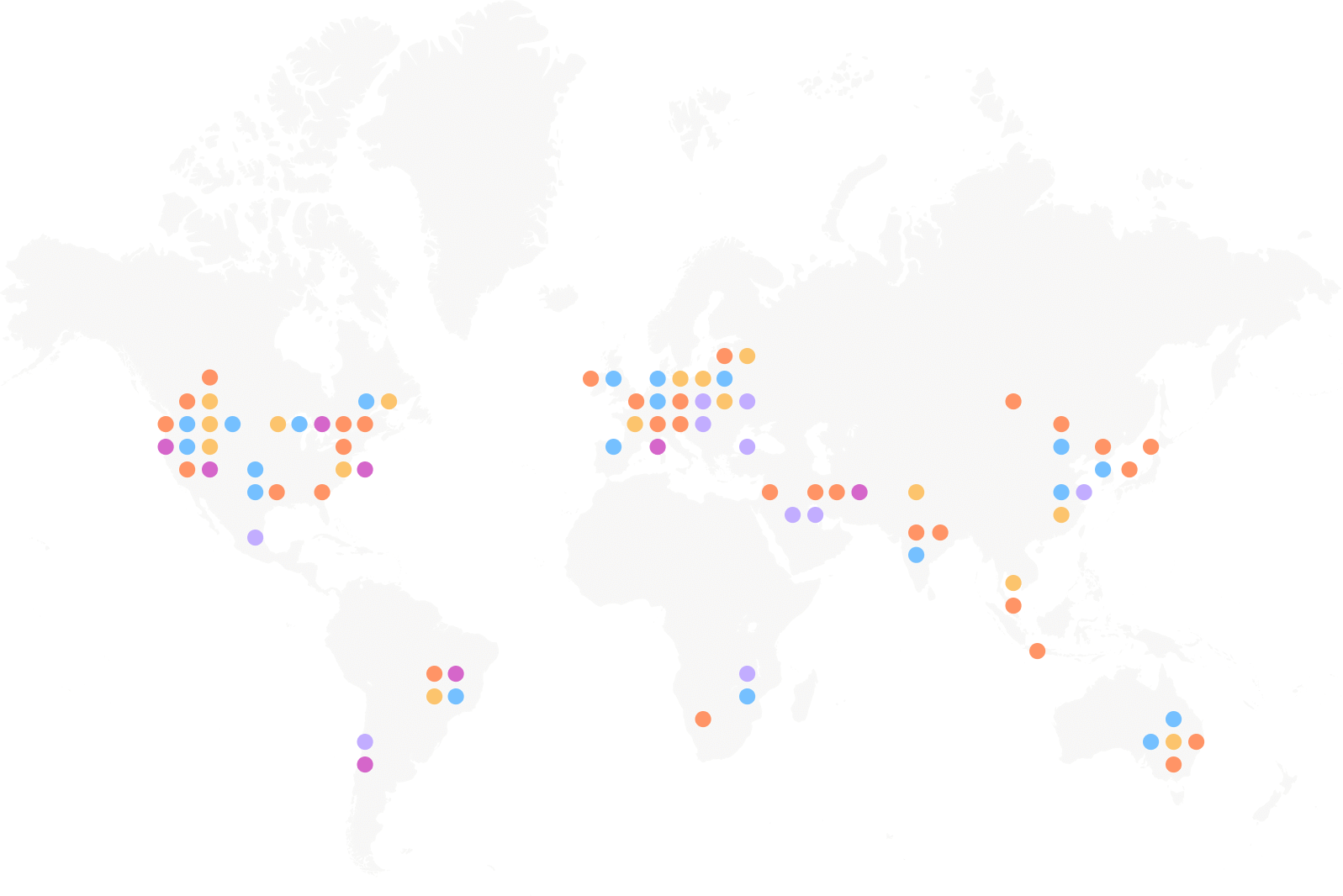
Scale globally
Atmos has 350 edge locations (across AWS, Azure, Google and Oracle), PoPs across 5 continents, and uses smart-routing as part of its full network-as-a-service.
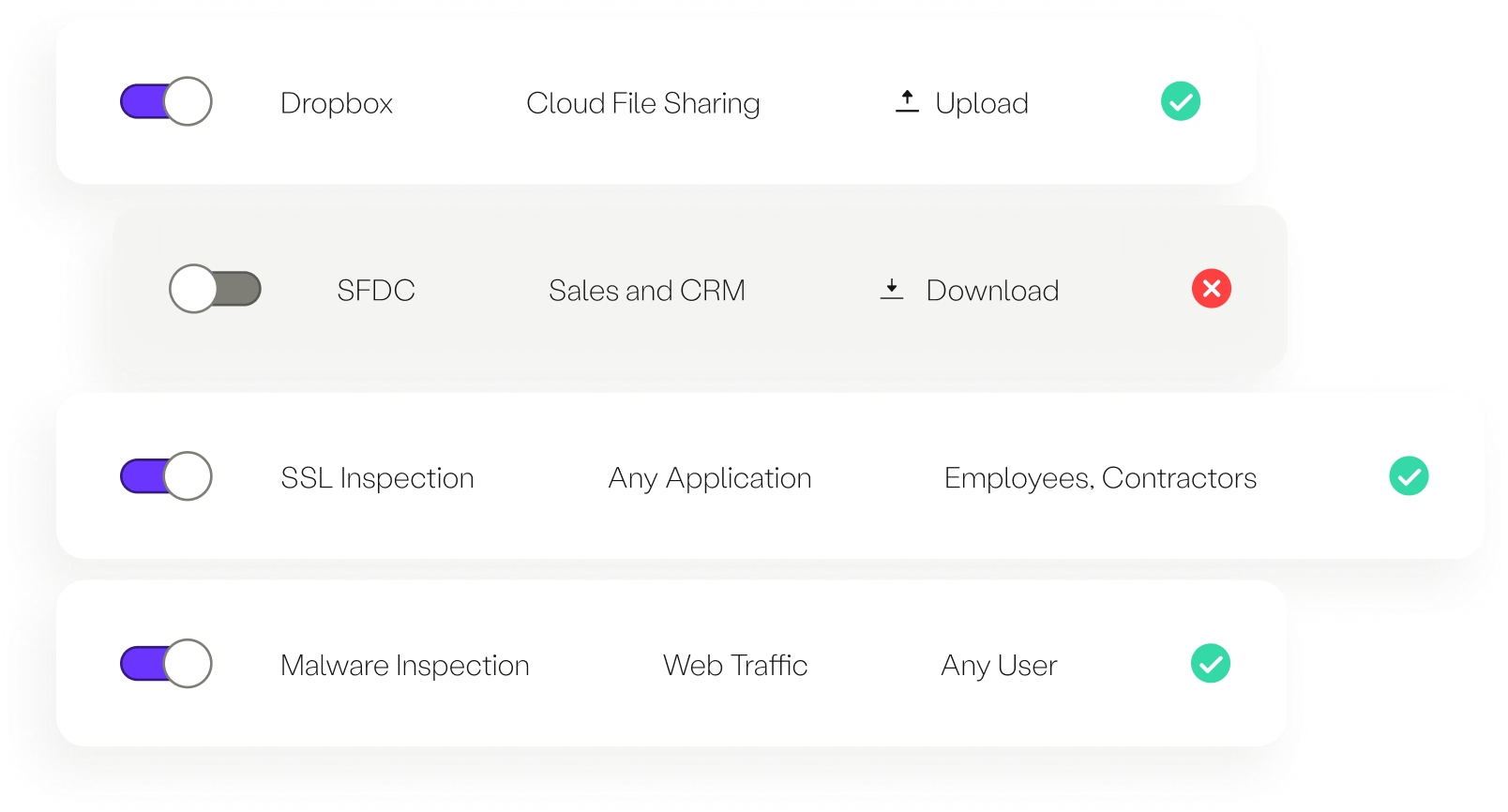
Data security
Protect against malware and data leakage using cloud-delivered web gateway and CASB capabilities like SSL inspection, malware scanning, and unified DLP controls.
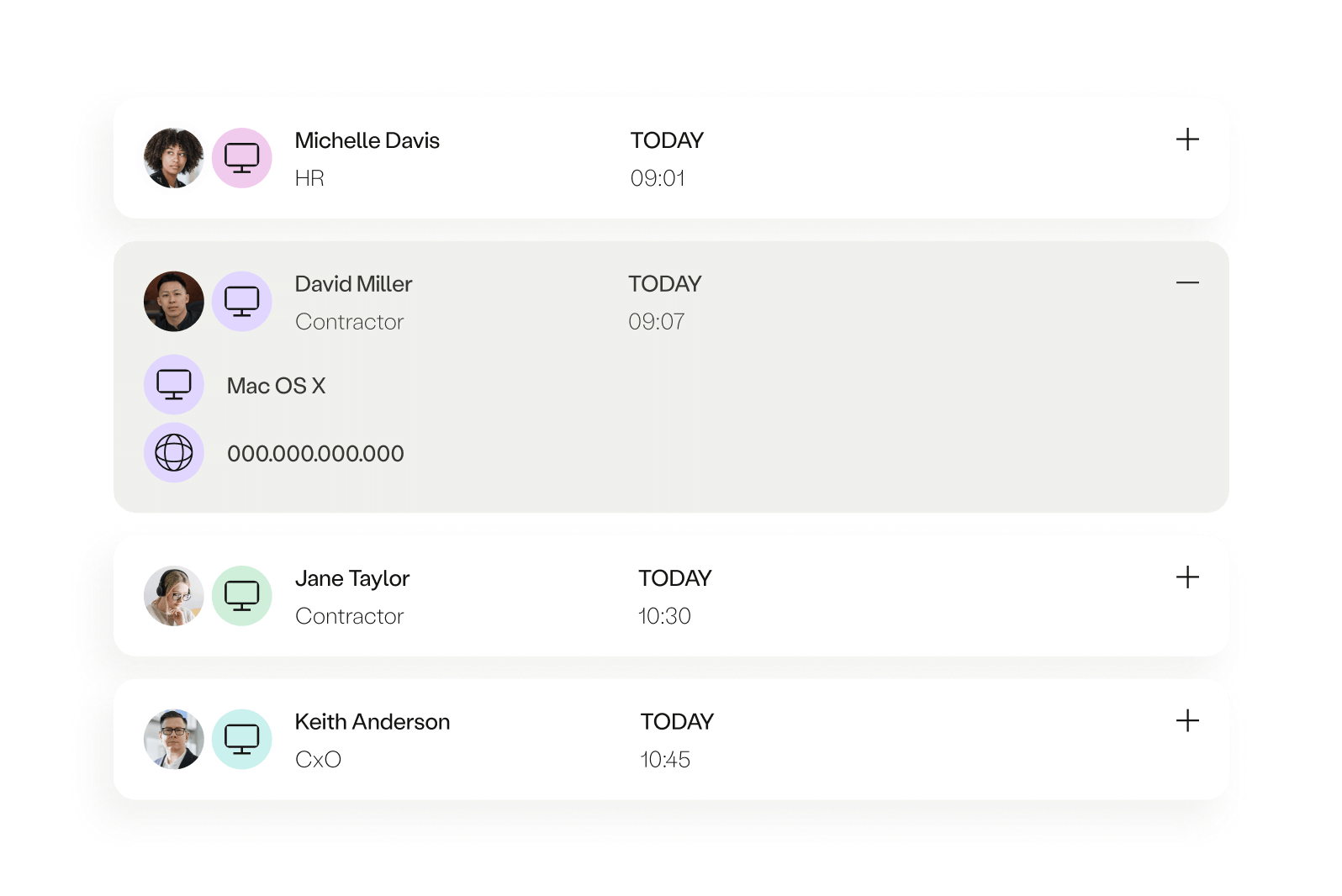
Deliver a great user experience
Monitor the digital experience of every user to proactively ensure high productivity, and reduce mean time to remediation.
Quick start
Top valued resources for your journey
FAQS
What role does Axis play in my zero trust strategy?
Zero trust is a combination of ecosystem technologies. Axis is the enforcement checkpost that integrates with your identity provider, and enforces access policies when a user attempts to access a specific app. We adapt access based on changes in context (device posture, geo-location etc.).
Can Atmos fully replace my remote access VPN?
Yes. One of the key Atmos ZTNA differentiators we developed was the ability to support all ports and protocols – even VOIP, ICMP, and AS400 applications. You have the ability to inspect all traffic as well, should you like to. We also developed Atmos Air, which is our agent-less capabilities. For example, SSH, RDP, Git and DB are all supported by Atmos Air. This also includes in-line controls like blocking file downloads. What this means is that our customers can remove VPN for remote access altogether. Even most VDI services as well.
Does Axis also provide SWG and CASB functionality as part of its service?
Yes. In addition to our Atmos ZTNA service, the Atmos platform also includes a full in-line secure web gateway (SWG) called Atmos Web Gateway for SSL inspection, URL filtering and malware scanning. For CASB, Atmos CASB is an in-line CASB for SaaS app discovery and data leakage prevention.
SSE or SASE? Do I need both?
Every customer is different. SASE is a combination of SSE (for secure access) and SD-WAN (for WAN optimization). About 70% of organizations who have a SASE strategy begin by first adopting a SSE service. They then make decisions on how best to solve for WAN Optimization, which often leads to a conversation around SD-WAN. Atmos’ IP Sec capabilities allows customers to integrate with and SD-WAN provider if, and when, needed. But, in general we recommend beginning with SSE, then deciding if SD-WAN is still a critical need for secure access needs.






