Secure Partner Remote Access & Vendor Access to OT
Vendors need access to resources,
not your network.

Protect operational technology from threats
Remote access solutions, like VPN, allow partners to directly access operational technology networks (OT) and industrial control systems (ICS) with very little security controls in place. This leads to an expanded attack surface, and risk of cyber attacks.

Protect the OT network.

Minimal exposure of critical infrastructure

Partner access, without network access

Enable access to OT systems from any type of vendor device

IT has visibility and control of what partners can and can’t access
Make business-critical OT networks
accessible, yet secure.
OT systems are critical to the operation of the business, and cybercriminals know that too. This is why 80% of IT leaders will adopt Security Service Edge (SSE) by 2025.
Enhance security
with least-privileged access for partner users
Enable remote access
for both managed or BYOD devices

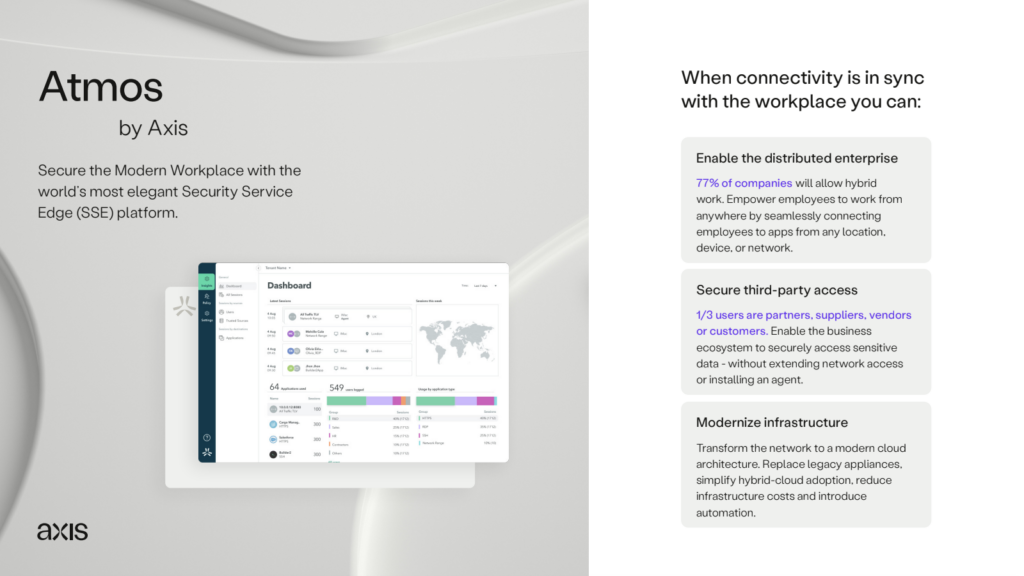
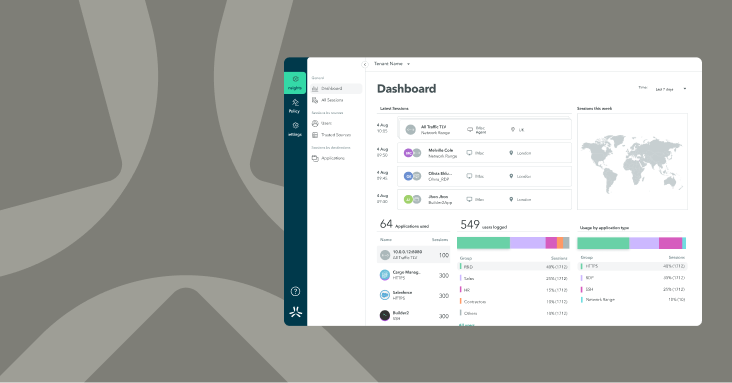
Enhance visibility
& simplify management of partner and OT activity
Minimize attack surface
by making OT systems invisible
Secure partner access and protect OT networks
The Atmos security service edge platform is designed to enable least-privileged access from contract users to business applications – without extending network access to the user.

Employs least-privileged access to reduce risk of security events
Protect business systems with full inline inspection, true app-level segmentation
Simplify partner access and IT lifecycle management through integrations (i.e SCIM)
Attain deeper visibility into partner and OT system activity