Making the Internet Safe for Work in a World Stricken with Ransomware
If you’re an IT security leader, this goes without being said – ransomware is the worst.
While the Internet continues to unlock new ways for businesses to increase routes to revenue, deliver great employee and customer experiences, and cut costs – cyber thugs have unleashed a slew of ransomware attacks that target legacy network architectures. Thus, these malicious attacks have been elevated to amongst the top of the list of business-level concerns.
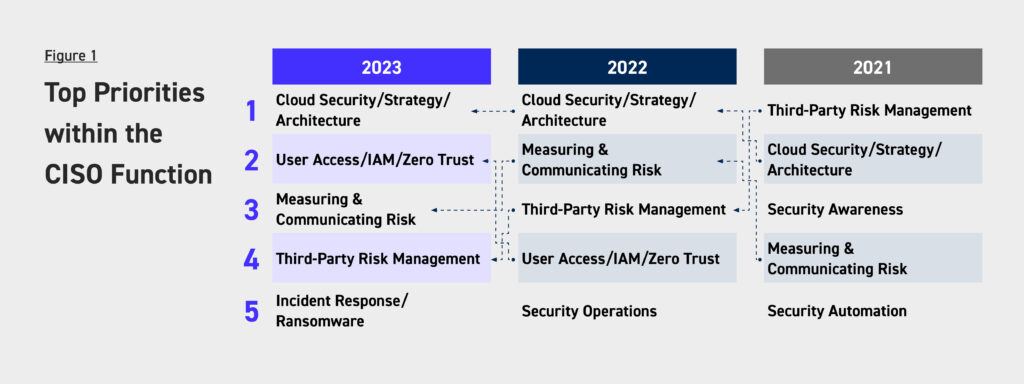
It’s the CISO who is tasked with defending the business from these threats. Hence why it’s no surprise, ransomware is one of the top 5 CISO priorities in 2023, as per a recent study from Evanta, by Gartner.
These attacks encrypt valuable data and hold it hostage, demanding a ransom for its release. The consequences of a successful ransomware attack can be devastating, resulting in not only financial losses, but also reputational damage, and significant operational disruption.
Over the last few years, ransomware attacks have inflicted significant financial losses on companies across multiple industries. According to this recent report by Cybersecurity Ventures, the global cost of ransomware is projected to reach $265 billion by 2031. That number is massive. For comparison, that amount would rank #42 out of 190 in a list of GDP rankings by country. The report estimates that a new organization will fall victim to a ransomware attack every 11 seconds in 2023.
These statistics highlight the urgent need for organizations to fortify their defenses against ransomware attacks. The rise in costs for ransomware damages over the last eight years is extremely alarming:
- 2015 – $325 Million
- 2017 – $5 Billion
- 2018 – $8 Billion
- 2019 – $11.5 Billion
- 2021 – $20 Billion
- 2031 – $265 Billion
Ransomware attacks use several techniques to infiltrate networks and compromise data including:
- Phishing Attacks: Phishing emails are crafted to deceive users into clicking on malicious links or downloading infected attachments, leading to the installation of ransomware.
- Remote Desktop Protocol (RDP) Exploitation: Attackers exploit vulnerabilities in RDP to gain unauthorized access to a system and deploy ransomware.
- Malvertising: The distribution of malicious advertisements redirects users to infected websites and triggers an automatic download of ransomware.
- Drive-by Downloads: Just visiting compromised websites can initiate the download and execution of ransomware without user interaction.
In my opinion, to protect against ransomware attacks effectively, IT security leaders should explore Security Service Edge (SSE) vendors that elegantly bring together three key services into a single platform: Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB):
Zero Trust Network Access (ZTNA):
ZTNA is a security model that enforces strict identity verification and access controls before granting access to applications. By implementing ZTNA, organizations can significantly reduce lateral movement by preventing unauthorized access to critical resources and by connecting users directly to applications rather than putting them and their devices on the network. Unlike legacy VPN tools, ZTNA solutions do not need to punch holes in the firewall and expose inbound ports thus significantly reducing the attack surface.
Secure Web Gateway (SWG):
A SWG is a gatekeeper between an organization’s internal network and the internet. It filters web traffic, scans for malicious content, and blocks access to risky websites. SWGs use advanced threat intelligence to detect and prevent ransomware attacks originating from internet-based sources. SWG enforces policies to prevent the downloading of suspicious files and actively block known malicious domains.
Cloud Access Security Broker (CASB):
CASB solutions provide visibility and control over data stored in cloud applications. With the increasing adoption of cloud services, it is crucial to secure cloud-based data from ransomware threats. CASBs enable organizations to monitor and protect data across multiple cloud platforms, enforce security policies, and detect anomalous user activities that could indicate a ransomware attack. CASBs also facilitate granular access controls to cloud applications, ensuring that only authorized users can modify or access critical data.
Take a look here to see what I mean. What you wind up with is the ability to effectively protect the business from ransomware. Below is the approach at Axis.
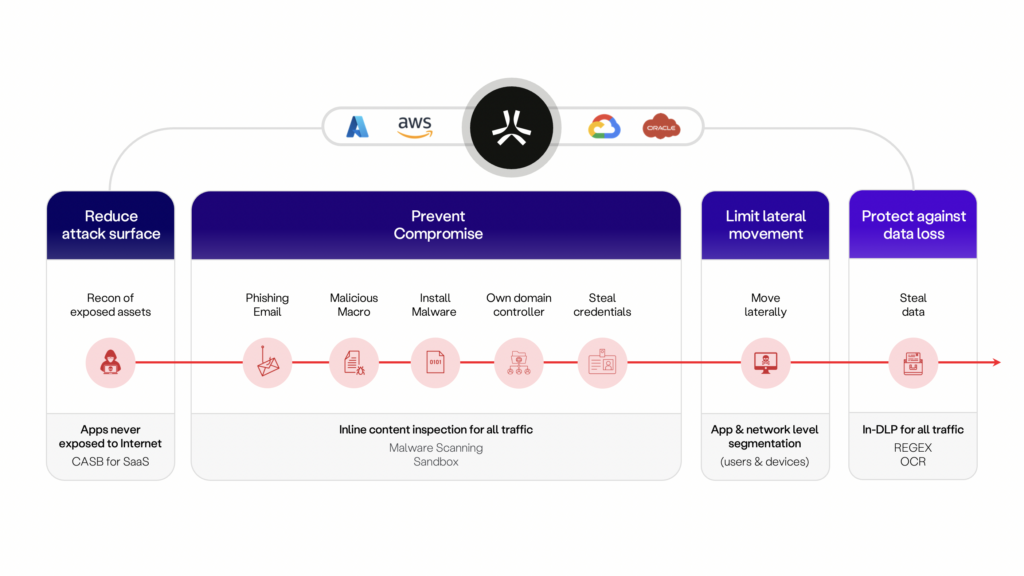
Ransomware attacks continue to evolve at an alarming rate and pose a severe threat to businesses worldwide. To mitigate this risk, businesses should adopt a proactive defense strategy that places SSE at the heart of it and combines ZTNA, SWG, and CASB into one elegantly delivered cloud service.
By implementing these technologies, organizations can significantly reduce their vulnerability to ransomware attacks and minimize the potential damage caused by such incidents.
Investing in the right measures is essential to protect valuable data, safeguard operations, and maintain the trust of customers and stakeholders in an increasingly Internet-connected digital landscape. Chief among them is SSE, the key to making the Internet safe for work.
Explore some of the new ways Axis Security is helping in our new 2023 Summer Release.