Finally say “buh-bye” to VPN
Finally say “buh-bye” to VPN
Axis ZTNA helps IT secure work from anywhere, without the pitfalls of VPN
Your opportunity to secure the modern workplace awaits

Enable universal
access to resources
Allow work from anywhere, on any device and over any network.

Enhance user
productivity
Ensure users have the best experience possible and avoid IT support tickets.

Save time
& lower costs
Use a cloud-delivered platform to avoid expensive firewalls and MPLS.

Protect data
from cyberthreats
Employ least-privileged access to resources without network access to prevent attacks.

Comparing Architectures
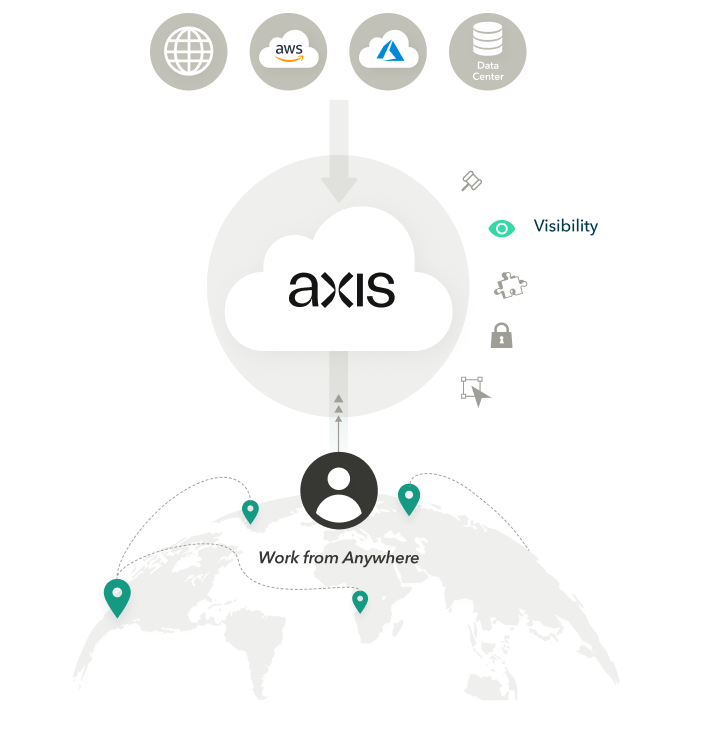
Integrations with IDP and always-on design creates seamless experience.
Brokered access to specific business resources via 350 PopS.
Users access apps, without access to the corporate network.
Apps are made invisible to unauthorized users by Axis.
Per application-level segmentation makes access simple to manage.
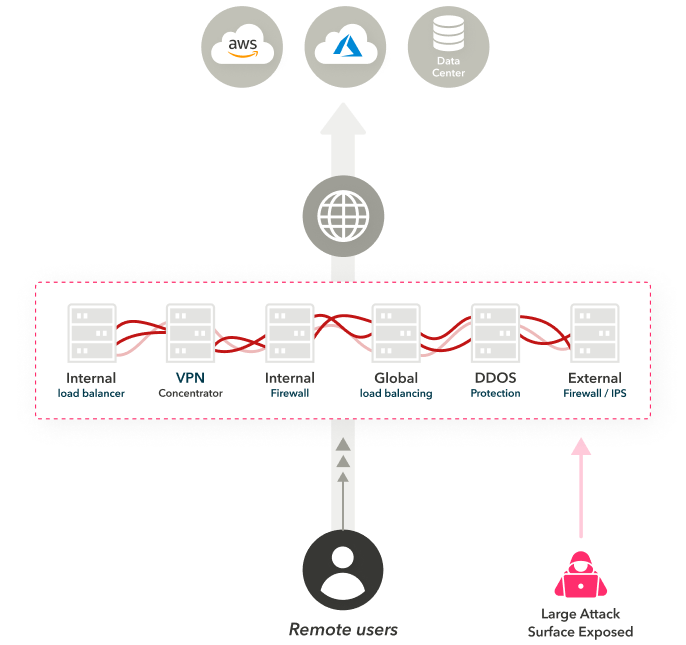
Users login repeatedly causing frustrating experience.
Traffic is backhauled to datacenter inhibiting productivity.
Inherent trust places employees and third-parties on corporate network.
VPN infrastructure is exposed to threats i.e. Ransomware.
Network segmentation is complex to manage.
See why with Axis,
you won’t be missing VPN.
Capabilities
Capabilities Comparison

Policy: Granular access
The platform provides granular policy access to specific applications, including:
- Device Posture Checks, such as personal firewall and disk encryption check.
- Conditions, such as destinations, time of day, location, and IP address range.
The platform provides granular policy access to specific applications, including:
- Device Posture Checks, such as personal firewall and disk encryption check.
- Conditions, such as destinations, time of day, location, and IP address range.

Continuous enforcement
The platform ensures continuous authentication throughout the session and not only at initial login.
The platform ensures continuous authentication throughout the session and not only at initial login.

Third-party access
The platform allows administrators to restrict access for contractors, temporary employees, BYOD devices.
The platform allows administrators to restrict access for contractors, temporary employees, BYOD devices.

Network isolation
The platform restricts access to individual applications rather than whole networks.
The platform restricts access to individual applications rather than whole networks.

Application isolation
Applications are published through the platform and are not exposed directly to the internet.
Applications are published through the platform and are not exposed directly to the internet.

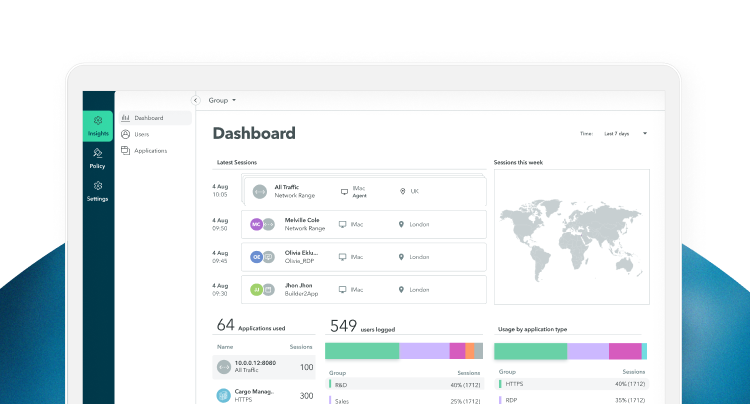
Visibility: Insights into user activity
The platform tracks all user activity to provide detailed views of network and application behavior, including URL history, SSH commands and file downloads.
The platform tracks all user activity to provide detailed views of network and application behavior, including URL history, SSH commands and file downloads.
Some of the Axis customers who have already said bye to VPN.




Need to find room in the budget?
Learn about our new VPN Buyback program
