Atmos. All of Your Secure Access Needs in One SSE Platform
Your team’s favorite security service edge (SSE) platform.
Designed to make access simple.
Short for “Atmosphere,” Atmos is the first SSE platform to elegantly integrate ZTNA, SWG, CASB and Digital Experience into a single, easy to use, interface.

What’s core, plus more.
Atmos ZTNA
Zero trust access to private apps
Atmos “Air”
Agentless access for BYOD and third-parties
Atmos Private Inspect
View user activity and block malicious activity
Atmos Server
Ensure servers safely communicate with other servers
Atmos Web Gateway
Zero trust access to Internet & SaaS
Atmos Cloud DLP
Protect sensitive data from leaking out to the Internet
Atmos CASB
Protect data, meet compliance needs, and discover Shadow IT SaaS apps
Atmos Advanced DLP
Use AI to receive alerts, auto-detect, and classify data
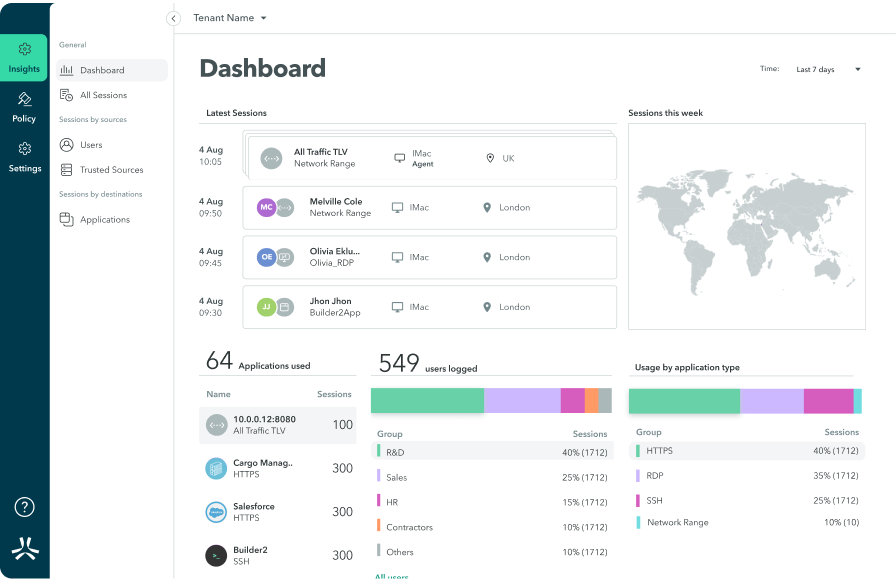
Atmos Dashboard
Manage all users, apps, servers and devices from a single pane of glass
Atmos Discovery
Shine light on unsanctioned private apps and reduce the attack surface
Atmos Experience
Monitor performance of devices, apps, and networks for the best experience
Atmos Insights
Visibility into each user’s activities, detect, view, and respond faster
Elegant workflow.
A user attempts to access
a business app
Secure access to major apps – even VOIP and ICMP – and support client or clientless access
Atmos mediates the request
Avoid passthrough connections that can lead to risk – Axis becomes the first stop
Atmos validates identity & policy
Adopt zero trust access and automatically adapt access rights based on changes in context (device posture, location etc.)
Atmos securely connects to
resource
Make private apps invisible to the Internet, keep users off the network, and deliver a safer connection to SaaS apps
Atmos inspects traffic
& monitors user experience
Get visibility into user activity so you’re aware of malicious activity, and ensure user experience is always great
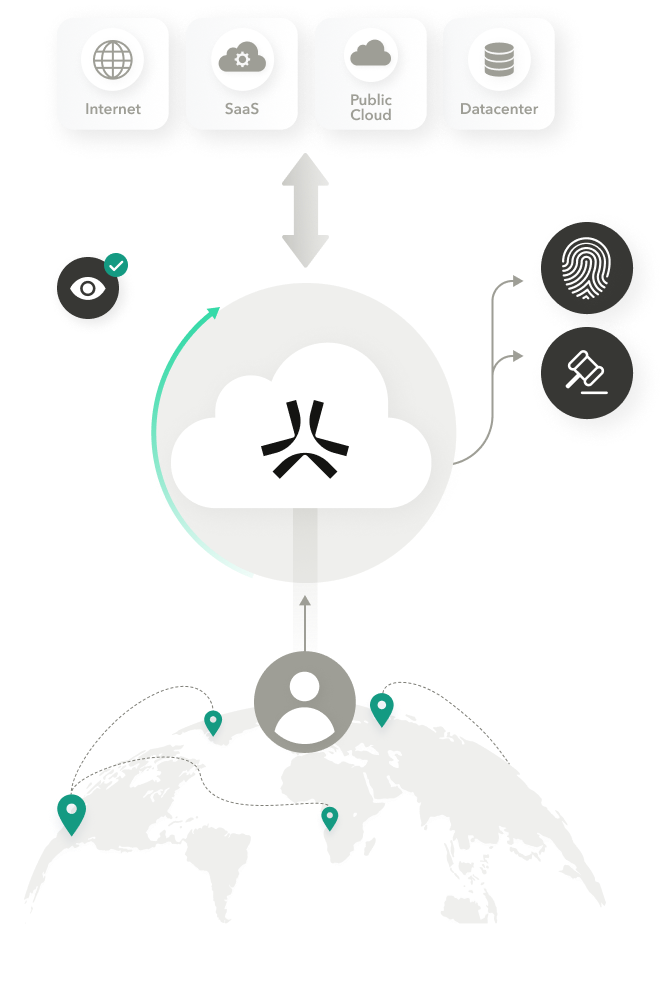
Ascend to Atmos
Multi-cloud backbone for scale
100% cloud-delivered with over 350 PoPs running on AWS, Google and Oracle. This ensures less latency, more redundancy and faster disaster recovery than any other SSE platform.
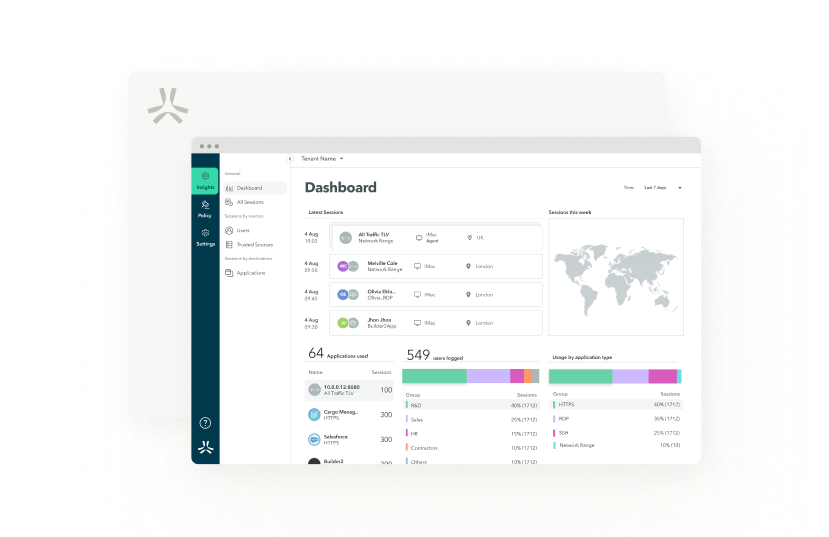
One interface, one policy
Atmos provides a , apps, devices, users, data, and more.
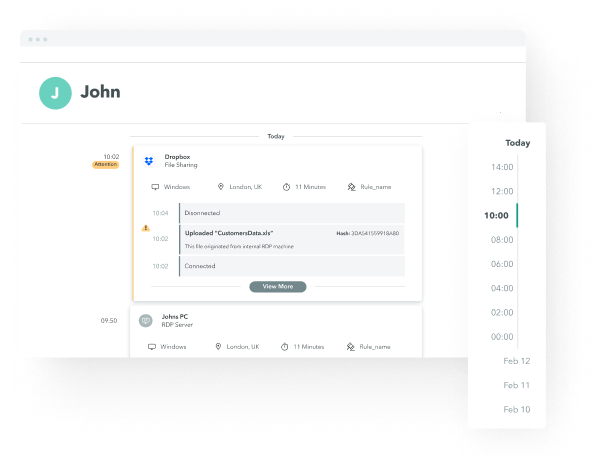
Unmatched visibility
Atmos inspects all traffic to provide visibility into user access across both internal and external apps so IT can prevent data leakage.
No app left behind
Atmos is the only service that supports all ports and protocols, even VOIP, ICMP, AS400 apps, and RDP, SSH, Git and DG via agentless web browsing – plus common SaaS apps and Internet protocols.

Auto-adaptive trust
Integrations with identity and endpoint security solutions enable context sharing across cloud services. If changes in identity or device health are detected, the Atmos access policies automatically adapt.

Innovation for differentiation
Cloud
With over 350 global points of presence running on the backbone of AWS, GCP and Oracle, the Atmos cloud securely connects any authorized users to any business application, based on simple to create policies.
Portal
The end user’s interface which, based on their identity and defined access policy, allows each user to see all their permitted agent or agentless applications – and easily connect to them with a click of a button.
Policy Tags
The Atmos logical tagging system helps IT admins define policies in minutes. Policies can reference groups of apps, or individual apps – making policy setting simple.
Agent
The Atmos Agent is a lightweight agent that runs on the end-users machine. The Agent performs device posture analysis, encrypts traffic, and then automatically forwards traffic to the Atmos Cloud. Atmos Agent continuously adapts access rights based on changes in context, and supports applications that require thick client access. The Atmos Agent can even support VOIP (peer-to-peer) and server-initiated (icmp) flows. For web-based applications, Atmos Agent is not required.
Connector
Often deployed in pairs, the Atmos Connector front-ends the customer’s private application. It provides a secure, outbound-only, and authenticated, connection between a customer’s application and the Atmos Cloud.
Confidence through compliance