Merger and Acquisition IT Solutions
Simplify your next M&A and divestiture down to just days.
Simplifying M&A and divestitures is a must.
When an organization acquires another company, Network and Security teams scramble to connect, and secure, disparate networks. Dealing with overlapping solutions and identity services can take upwards of a year.
As M&A and divestitures continue to take place, IT must do everything possible to avoid integrating networks, and implement simple ways to standardize security practices across entities.
M&A is a massive opportunity for IT to provide value.

IT must move fast while under strict budget restrictions

Time to value is critical. But least-privilege access to key systems is just as key

Visibility must improve despite disparate networks and systems

Overlapping networks and IDPs are must be avoided in M&A scenarios
Actually look forward to the next company announcement.
Accelerating IT integration during an M&A or divestiture calls for the right balance of speed, security, and coordination between teams.

Reduce risk
Introduce zero trust access to reduce risk of acquiring a data breach, and to standardize security levels

Minimize downtime
Grant new users access to critical apps like HR, Payroll and Benefits, in just minutes, not months or years

Avoid complexity
of integrating networks, , or deciding who’s gear to use
Gain visibility
Gain better visibility in what users are accessing, and take control so you can protect sensitive data from leaking out
Make life easier with Atmos.
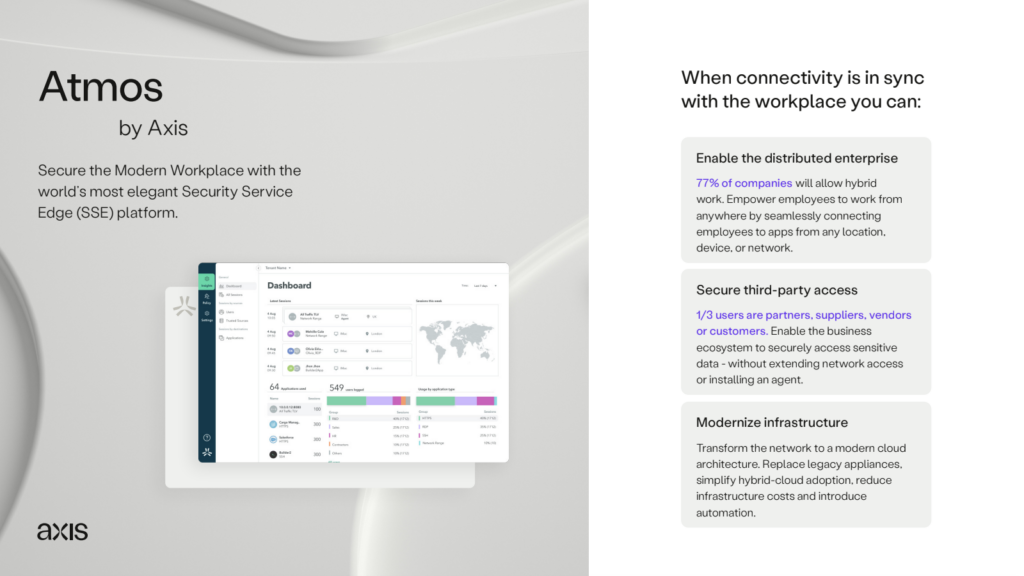
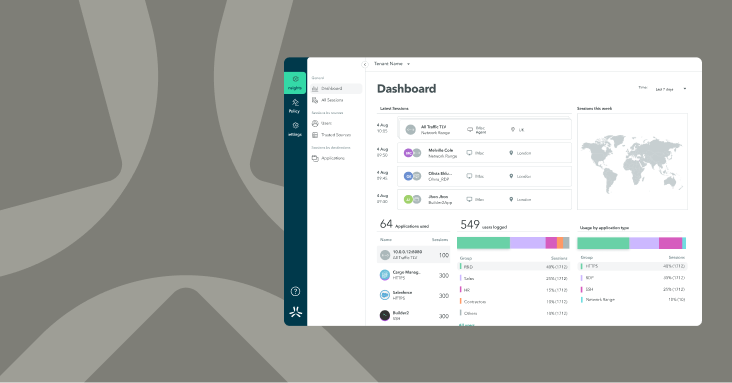
The Atmos platform eliminates the complexity of network integrations, overlapping IPs, and managing multiple identity systems. The cloud architecture uses identity and policy to automatically determine which users should get access to sensitive data, and delivers a seamless experience.
Use policy-tagging to easily define which user groups access business apps
Provide new users with same day access to SaaS, Web and private applications used for work
Easily comply with security standards by inspecting traffic to ensure nothing bad comes in, and nothing good leaks out
Monitor device, application, and network performance to make sure the onboarding experience is smooth
Integrations help simplify identity lifecycle management