Secure Contractor Access
Enable least-privileged access for contractors needing access to business resources.

Contracting risk
The average employment tenure for contractors is ten weeks. This isn’t much time to get them on-boarded and ramped-up.
Because remote access solutions, like VPN and VDI, give external users full network access, these over-privileged users become a high risk to the enterprise.
For most companies,
access is overextended to contractors

51% of organizations have experienced a data breach caused by a third-party

74% say that a security breach was caused by over-privileged access to third parties

63% of organizations don’t know the level of access and permissions of internal and external users

59% of respondents say there is no centralized access control over third-parties
Eliminate over privileged access
Your contract users only need access to specific applications, so keep them off the corporate network altogether. In order to keep your network and business free of risk, connectivity must be segmented, simple, controlled, and powered by zero trust.

Enforce least-privileged
not with complex network segmentation, but granular app segmentation based on policy
Leverage agentless capabilities
give access flexibility without compromising security

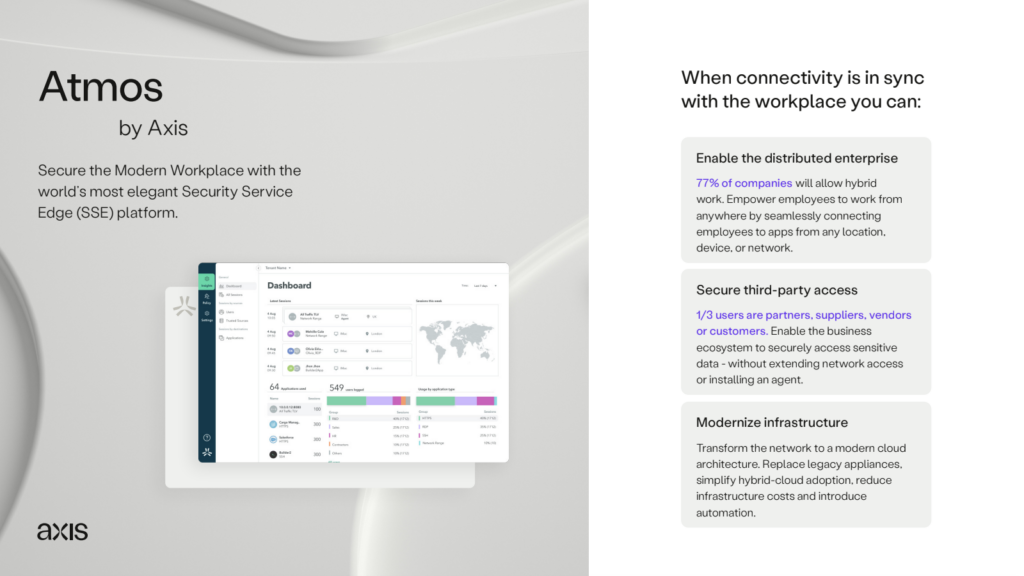
Regain IT control
and enhance visibility into all contractor activity
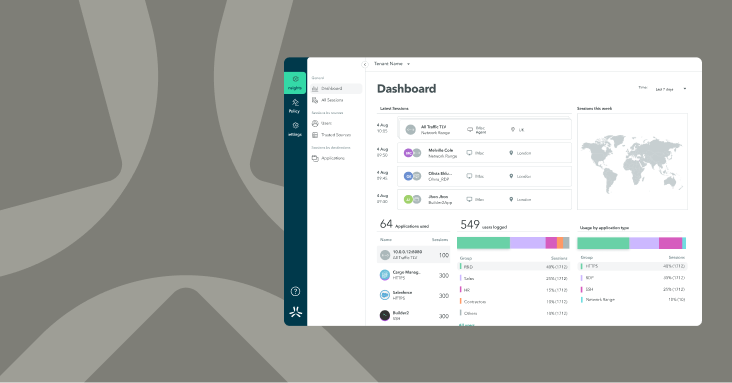
Securing contractor access
is simple
The Atmos security service edge platform is designed to enable least-privileged access to business applications – without extending network access to the third party user.

Employ least-privileged access to reduce risk of security events – all without placing contractors on the corporate network
Protect business data through full inline inspection, and true app-level segmentation
True agentless access with the ability to simplify partner lifecycle management through integrations like SCIM
Attain deeper visibility into partner activity and insights into access experience