Why I Migrated from ZTNA 1.0 to Modern Day ZTNA
ZTNA – The Beginning
In 2017 Gartner unveiled a new acronym “ZTNA” short for zero trust network access, and released the Market Guide for Zero Trust Network Access. Revolutionary, especially compared to its incumbent technologies like VPN, ZTNA solution quickly became a new form of remote access that was designed to replace traditional remote access technologies and all the risks they came with.
The core concept of a ZTNA platform was to minimize a company’s attack surface, and provide users with access to the applications they need without putting them on the network and allowing lateral movement.
Since 2017 the number of vendors has increased significantly and the world has changed drastically with users accessing data and applications from anywhere at any time.
This means that the solutions design and development back in 2017 when the world was very different, let’s call them ZTNA 1.0 solutions, worked for a time, but have quickly become dated due to their lack of key functionality, and complex deployment processes.
The Prius became the Tesla, Blockbuster became Netflix, maps became satellite navigation, now I believe it’s time for those ZTNA 1.0 solutions to be replaced by modern day ZTNA ones instead.
My Story
Flashback to 2019, before the world got weird, I was working at a multinational organization running global infrastructure and as our contract was up for renewal we were about to embark on a global network refresh. Our goal was to reduce costs by moving away from our expensive and slow MPLS solution as well as our legacy VPN and SWG solutions. One of our biggest use cases was finding a way to better support and secure access for both our remote and third-party users who were currently using VPN.
Our legacy VPN solution had no MFA, no posture checking, had policies that were complex, difficult to configure, and had no granularity. It was on a binary choice of on the network or not on the network. Once people opened the VPN they simply got dropped on the network and could do anything they wanted. It also meant we had to publish systems to the internet and therefore opening ourselves up for attack.
As the project began our global network provider advised us to consider a Zero Trust Network Access (ZTNA) offering as an alternative to the legacy VPN. As ZTNA was a very new concept in the UK I did many months of background reading, investigation, meetings and whiteboarding sessions. During that time we were introduced to the vendor Zscaler, and after around six months of design work, testing, and discussions I was ready to propose the solution to the management team.
In January 2020 we decided to move forward with a combined global rollout of a SD-WAN solution as well as Zscaler Private Access (ZPA) for remote access and Zscaler Internet Access (ZIA) for internet access.
ZTNA 1.0 Challenges
At the time we understood that ZTNA 1.0 wasn’t going to be a perfect solution, but options were limited and at that point anything was better than our legacy VPN solution. However, we did encounter some challenges.
- Wasn’t a 1-for-1 VPN replacement – The solutions struggled to support some legacy applications such as VOIP and it could not deal with server to client traffic and only dealt with client to server. This meant that it didn’t support all the applications we needed them to such as VOIP and systems that had server initiates flows.
- Complex to manage day-to-day functions – The ZTNA and the web gateway solutions had been developed independently, which meant that we had to perform administration tasks via several separate consoles. This added complexity and made managing them far more challenging.
- Limited agentless functionality – The number of protocols available agentlessly was very limited. Didn’t have support for RDP for example. This meant it was difficult to configure access for 3rd parties or contractors where it was difficult to run agents meaning in some cases we had to resort to either having them install agents or making the costly choice of sending them corporate computers which were then hard to support and manage.
- Hand-off to other teams was difficult – It was hard to hand the system over to the BAU team as due to the complexity of managing the system future changes needed an in-depth knowledge of the platform. As stated before to make changes you needed understanding and access to several different portals and because policies were complex to manage it meant that only those with implementation experience could configure them to avoid misconfigurations.
These challenges meant we quickly recognized that whilst it was a better solution than our old legacy VPN solution, ZTNA 1.0 wasn’t quite the fit that we needed. We needed a solution that was more mature.
Mindset shift to a Modern Day ZTNA
While my company encountered the challenge of being an early adopter of ZTNA, many companies today can benefit as a result of the advancements of Modern Day ZTNA solutions. Modern ZTNA solutions have the benefit of optimizing and overcoming where ZTNA 1.0 failed. Based on my experience with ZTNA 1.0 and the challenges faced, here are my recommendations when looking for a modern day ZTNA solution:
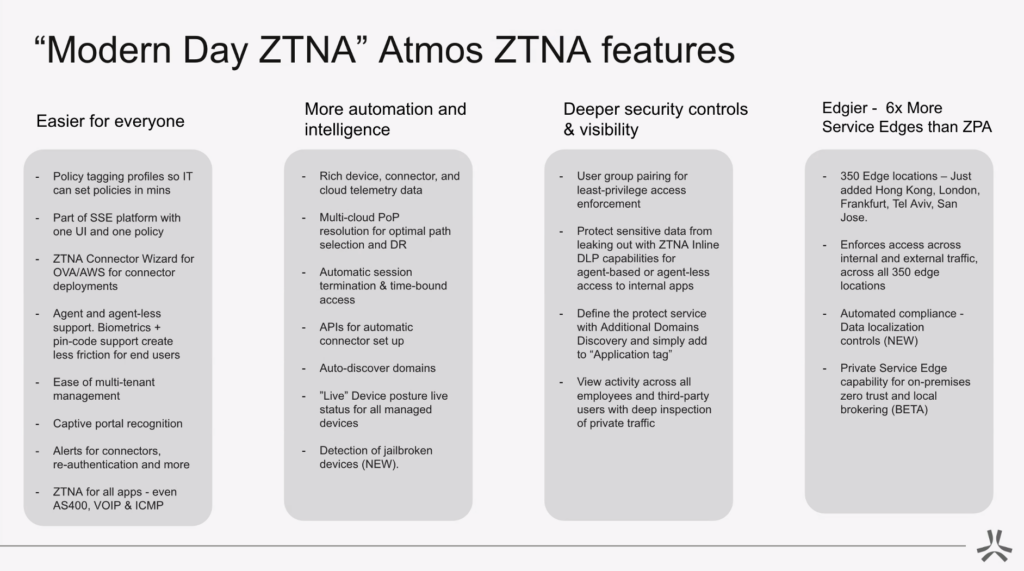
- Pick a solution that is easier for everyone – It’s important to consider a ZTNA solution that not only is easy to use from an IT and admin perspective, but also from an end-user point of view. For IT professionals, this might look like having a single management console for administration instead of separate portals. This could also mean including features like Additional Domain Discovery which cuts down the time to onboard applications by removing the need to complete this task by trial and error. For end-users, easy ZTNA access could look like having a wide-support of agent AND agentless capabilities for apps like AS400, IMCP, VOIP, SSH, RDP, Git, etc. Consider features that make verification easier with biometric and pin-code support which makes access more frictionless for the end-user.
- Prioritize automation and intelligence – The tool should help make people’s lives easier. You should consider things such as multi-cloud PoP resolution for optimal path selection and DR, automatic session termination and time bound access, tools for automatic connector deployments, device posture for all devices and detection of jailbroken devices.
- Seek out deeper security controls & visibility – In a world where data and systems are everywhere on premise monitor and control solutions are no longer viable. Look for a solution that allows you to view activity across all employees and third parties with deep inspection of private traffic and the ability to protect sensitive data from leaking out with inline DLP capabilities for both agentless and agent access to internal applications.
- Be aware of size! Service edge locations matter
Moving Forward
As outlined above older ZTNA 1.0 solutions come with challenges and it’s my feeling that it’s time for us to look at these the same way as we look at legacy VPN solutions. They are no longer fit for the world we live in. Now is the time for a solution built today for today.
At Axis we understand that switching from what should now be seen as legacy ZTNA 1.0 solutions to a modern-day ZTNA can be daunting and this is why they have developed the world’s first ZTNA migration tool to make things simpler, especially for customers of Zscaler Private Access (ZPA). The Atmos Migration Tool takes application segments developed in Zscaler Private Access (ZPA), and allows them to be mapped into the Atmos ZTNA service where policies can then easily be developed using our policy tagging system – all within just a few minutes.
With these tools now available to you, there is nothing to hold you back from trying a modern-day ZTNA. Schedule a demo and ask us how we can help.
Want to learn more about the modern-day ZTNA?