How to Prepare for The Evolving Threat of Ransomware
Three zero trust tips to help protect against sophisticated attacks from Russia.
Last week, when Russia advanced past Ukrainian borders we began to hear about the coordinated, hybrid attacks – spanning both cyber warfare and physical warfare – that lead up to the event. Phishing emails sent to the State Administration of Seaports of Ukraine sent earlier in February as a sort of advanced attack against Ukrainian ports. A new data wiper malware installed on hundreds of machines across Ukraine – reported within hours of Russia invading.
A malicious concoction of tools used to create disarray while striking fear and uncertainty into Ukraine.
The growing threat
The US, and its allies, have since announced that they have imposed sanctions on Russia as a sign of disapproval of the conflict. Given Russia’s demonstrated history of using advanced persistent threats to threaten critical infrastructure, US cybersecurity leaders have asked companies to remain vigilant, and to take action to improve their defense against the potentiality of retaliatory attacks against US businesses.
While no official decision has yet been made at the time of this blog, it’s also worth mentioning that there could be more sanctions on Russia coming down the pipe. There are talks about the possibility of removing Russia from the SWIFT banking system. Formed in 1973, SWIFT connects more than 11,000 financial institutions in more than 200 countries and territories worldwide so banks can be informed about transactions.
According to USA Today “Barring Russia from SWIFT would damage the country’s economy right away and, in the long term, cut Russia off from a swath of international financial transactions. That includes international profits from oil and gas production, which make up more than 40% of Russia’s revenue.”
This could place financial pressure on Russia, causing them to resort to alternative sources for revenue. One of which could be ransomware.
Understanding the risk landscape
I applaud the CISA, FBI and the NSA for joining together to help IT security leaders reduce the risk of potential ransomware threats. The January 11th advisory alert (AA22-011A) and February 16th advisory alert (AA22-047A) demonstrate that US leaders are doing everything they can to provide information to public agencies and private sector companies to help protect critical infrastructure against the expected increase in Russian State-sponsored attacks.
We recommend that all companies, especially those who do business in Ukraine, remain particularly vigilant. It’s widely known that Russian State-Sponsored advanced persistent threats (APTs) have been used to exploit several traditional access solutions as a means of gaining access to networks, and unleashing ransomware attacks that propagate across them. Once on the network, the threat can lock down the victim’s critical infrastructure or sensitive data. The advisory alerts remind its readers of the vulnerabilities known to have been exploited in the past. See some examples below:
- CVE-2018-13379 FortiGate VPNs
- CVE-2019-1653 Cisco router
- CVE-2019-2725 Oracle WebLogic Server
- CVE-2019-7609 Kibana
- CVE-2019-9670 Zimbra software
- CVE-2019-10149 Exim Simple Mail Transfer Protocol
- CVE-2019-11510 Pulse Secure
- CVE-2019-19781 Citrix
- CVE-2020-0688 Microsoft Exchange
- CVE-2020-4006 VMWare (note: this was a zero-day at time.)
- CVE-2020-5902 F5 Big-IP
- CVE-2020-14882 Oracle WebLogic
- CVE-2021-26855 Microsoft Exchange (Note: this vulnerability is frequently observed used in conjunction with CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065)
It’s important to note that the examples above highlight how phishing emails are not the only tactics that sophisticated threats actors are utilizing. The below image explains the anatomy of how Phishing-based attacks and VPN-based breaches work.
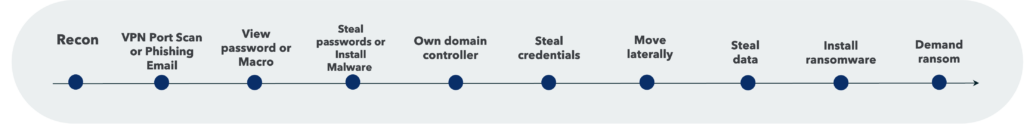
Several companies have reached out to us for guidance. We’ve prepared some tips for how to help them protect themselves from sophisticated attacks, in addition to the recommendations from CISA, FBI and NISA.
Three ways zero trust protects against ransomware
- Reduces the attack surface: You can drastically reduce the risk of ransomware if you can minimize the attack surface by ensuring that your apps are not exposed to the open Internet. This means removing remote access technologies that require placing users on the network (a large reason why ransomware attacks succeed), and replacing them with a zero trust network access (ZTNA) service.
Security Tip: This reduction in attack surface should be coupled with the ability to also inspect, and if needed, block malicious exploits lurking in SSL. By both reducing the need for connectivity, thus minimizing the attack surface, and inspecting traffic, you’ll be able to better protect your environment. - Reduces lateral movement: Aside from reducing exposure to the Internet, you can also reduce the blast radius of a threat. This is where per app segmentation comes in. ZTNA services that offer this level of segmentation allow you to ensure that remote employees, or third-parties, are never placed onto the corporate network. Customers have a built-in means of both preventing ransomware threats from accessing the corporate network, and completely reducing the chance of the threat moving laterally across the LAN.
Security Tip: Ensure that the zero trust vendor you are using for access has per app segmentation ability. Some zero trust solutions can only provide access to an application server, not an individual application. If that’s the case, sophisticated attacks can still reach other applications running on the same server. Additionally, zero trust vendors that use virtual firewalls to inevitably connect traffic to a network are still susceptible to ransomware threats. Avoid these types of solutions. - Reduces data loss – You can protect sensitive data from being exfiltrated by ransomware with a zero trust service with inline inspection and DLP controls that disable download, block copy & paste if data, and tell you right away what data, if any, is being exfiltrated to an external source.
The below image showcases the three ways that zero trust protects against ransomware threats, in practice.
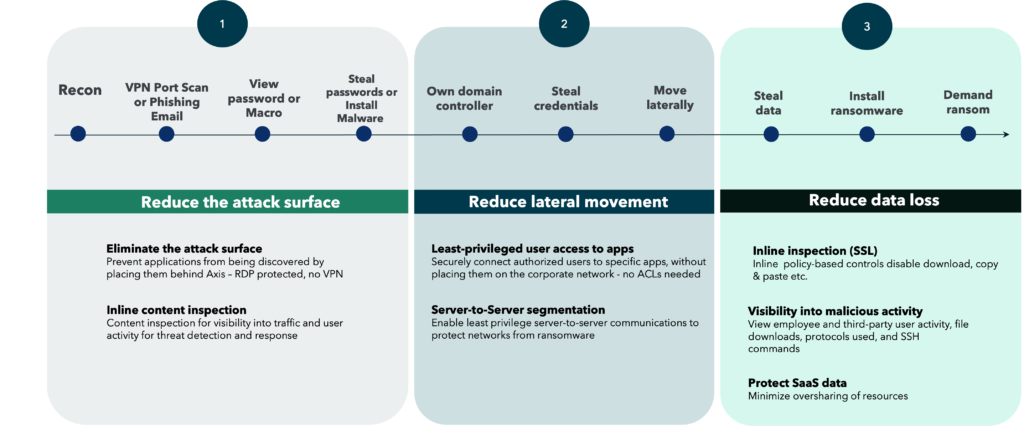
With the proper zero trust access solution enterprises, and government agencies, can better protect themselves from ransomware threats.
As the world hopes for a peaceful resolution we must also prepare ourselves for a new reality. One where targeted ransomware threats increase. Please make sure you have a plan in place, and that it involves embracing zero trust within your environment.
To learn more about zero trust, and experience it for yourself, request a free demo from our team – https://www.axissecurity.com/schedule-a-demo/