Architecting to Protect Against Ransomware
So, for anyone that has been in IT for the last 10+ years, you will know that the risk of ransomware and cyberattack is not something new. It’s been on our radar as a top concern for many years. The difference now is the prevalence of attacks on large global companies which has raised this security issue all the way to the Board of Directors.
A few months ago, when Russia invaded Ukraine, our concerns became something the whole world rather than just IT started to hear about. It was reported on the news that cyberattacks were being used by both sides and within hours of Russia invading, it was announced that a new data wiper malware had been installed on hundreds of machines across Ukraine by Russia.
Next came sanctions imposed by the west on Russia as a sign of disapproval of the conflict. Given Russia’s demonstrated history of using advanced persistent cyberattacks, US cybersecurity leaders asked companies to remain vigilant and take immediate action to improve their defenses against the potentiality of attacks against businesses.
However, it’s important to note that these are just a few examples, and they are not the only tactics that sophisticated threat actors are utilizing. More than ever, large companies are subjected to cyberattacks and this has been accelerating in the past year.
Legacy infrastructure with large attack surfaces that allow for lateral movement has proven to be an irresistible target for attackers. An attacker can easily sweep the internet scanning for open ports to attack or send mass batches of phishing emails. If they can penetrate the network or install malware the door is open for them. They can roam around on the network and extract data without anyone ever knowing they have been there.
Many companies have solutions from multiple vendors to try and resolve these issues but monitoring and managing these systems, keeping them updated, and reacting to any issues is very time-consuming and expensive. It’s like putting your finger in a leaking dam. The old way of doing things just no longer works.
With the risk of being attacked increasing, we need a better way of architecting to protect against ransomware. We need to minimize the attack surface by ensuring that applications are not directly exposed to the open Internet. The reduction in attack surface should be coupled with the ability to inspect, and if needed, block malicious exploits lurking in SSL.
We need to remove remote access technologies that require placing users directly on the network and replace them with technologies that give the least privileged access to applications. And we need tools to protect sensitive data being exfiltrated with inline inspection and DLP controls. We need to be able to disable upload and download as needed, block copy & paste of data, and be able to tell what data, if any, is being exfiltrated to an external source.
At Axis, we believe we can resolve many of these issues. We place a lightweight connector in front of the applications, and they are published to the required users. Only the application, at a granular level, not full network access. The user requests access to an application and Axis mediates the initial connection, this is key to zero trust. There are no passthrough connections allowed. The user’s identity is verified, and access is validated based on policy and context, such as user identity, device health, application type, and even the user’s location.
The service then brokers a 1:1 outbound connection between a specific resource and an authorized user. The key is that this is granular. There is no network access. Traffic is inspected throughout the session which means if anything changes, such as the user’s IP address, they are removed, or the device posture access is revoked. We can configure DLP controls that disable upload and download as needed, block copy & paste of data, and have the ability to tell you right away what data, if any, is being exfiltrated to an external source.
With the tools we have, working in harmony, we are able to significantly reduce the risk of ransomware as highlighted below:
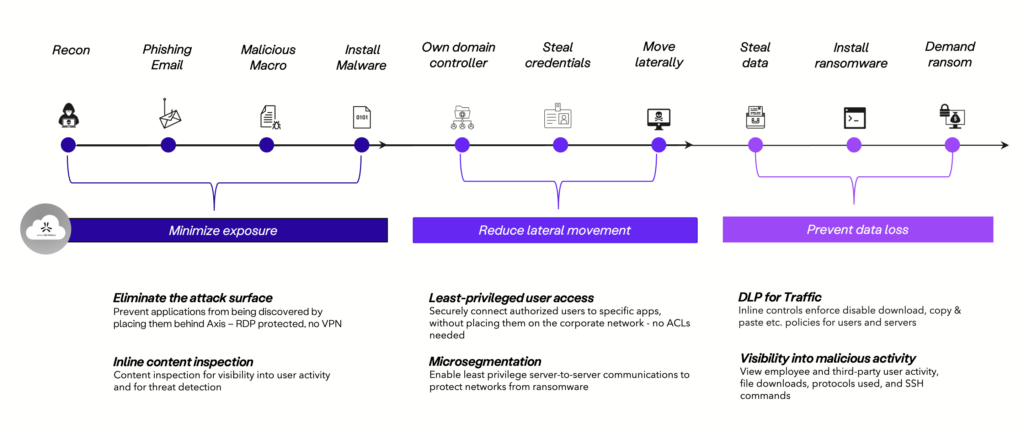
It’s worth noting that, unlike some zero-trust vendors, Axis has per-application segmentation ability. The competition can only provide access to an application and not an individual application. If that’s the case, sophisticated attacks can still reach other applications running on the same server. Additionally, zero-trust vendors that use virtual firewalls to connect traffic to a network inevitably are still susceptible to ransomware threats due to the visible attack surface that is still present.